In the dynamic landscape of today’s business world, Software as a Service (SaaS) applications have become the bedrock of efficiency, driving operational agility and competitiveness. Yet, amid this digital transformation, a looming concern casts a shadow – the security of sensitive data within these expansive SaaS ecosystems.
The urgency of this concern is underscored by some striking statistics:
- A McAfee report paints a stark picture, revealing that organizations, on average, confront a staggering 31.3 cloud-related security incidents every month.
- Gartner, a global technology research firm, echoes this alarm with its finding that a staggering 80% of businesses suffering cloud data breaches attribute them to misconfigurations and human errors, rather than the negligence of cloud providers.
- The Ponemon Institute, renowned for its research on data breaches, delivers a sobering statistic: the average cost of a data breach amounts to a hefty $3.86 million, a financial blow that can be especially crippling for businesses across the spectrum.
The era of SaaS proliferation has unfurled new horizons for enterprises, but it has also unveiled vulnerabilities that can’t be overlooked. As technology marches on, so does the sophistication of cyber threats. With businesses relying on SaaS more than ever, the need to fortify these digital ramparts is paramount.
Amid this backdrop, the array of SaaS security solutions available can be both a blessing and a puzzle. Choosing the right solution is not only about plugging gaps but also about aligning with your organization’s unique needs, financial considerations, and security prerequisites.
The Dichotomy: Efficiency vs. Vulnerability
SaaS platforms undeniably present a double-edged sword for businesses. On one hand, they empower employees with easy access to a suite of powerful tools, fostering innovation and productivity. On the other hand, the distributed nature of cloud-based applications exposes sensitive data to new attack vectors. According to a survey by McAfee, over 80% of organizations experienced at least one compromised account threat within the span of a year. This stark reality highlights the pressing need for robust SaaS security solutions to effectively mitigate risks and ensure data integrity.
Nurturing Security Parity: Protecting Data and Navigating Compliance
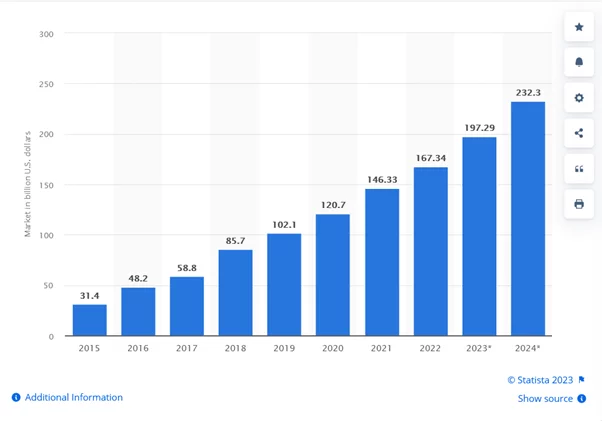
Public cloud application services/software as a service (SaaS) end-user spending worldwide from 2015 to 2024
As organizations navigate the intricacies of the digital era, the need to safeguard sensitive data assumes paramount importance. Compliance regulations like GDPR and CCPA further underscore the imperative of instituting stringent security practices to ensure the privacy of customer information. A study by IBM indicates that the average cost of a data breach is $4.72 million, magnifying the potential repercussions of inadequate security measures. Hence, deploying effective SaaS security solutions becomes a strategic imperative, bridging the gap between efficiency and vulnerability.
- Protect Sensitive Data: SaaS applications often handle sensitive business and customer data. SaaS security solutions help safeguard this data from unauthorized access, data breaches, and data leakage, ensuring data privacy and compliance with regulations.
- Mitigate Cyber Threats: Cyber threats like phishing, malware, ransomware, and insider attacks target SaaS applications. SaaS security solutions offer advanced threat detection, real-time monitoring, and proactive measures to detect and mitigate these threats effectively.
- Ensure Compliance: Various industries have stringent compliance requirements, such as GDPR, HIPAA, and PCI DSS. SaaS security solutions help organizations adhere to these regulations by enforcing data protection policies, access controls, and audit trails.
- Secure User Authentication: SaaS security solutions offer multi-factor authentication (MFA) and single sign-on (SSO) capabilities. These enhance user authentication, reduce the risk of unauthorized access, and prevent account hijacking.
- Manage Access Controls: With a myriad of users accessing SaaS applications, it’s essential to manage and control their access based on roles and responsibilities. SaaS security solutions allow organizations to define granular access controls to limit data exposure.
- Prevent Data Loss: Data loss can occur due to accidental sharing, insider threats, or unauthorized access. SaaS security solutions implement data loss prevention (DLP) measures, including encryption, access restrictions, and policy enforcement, to prevent data leakage.
- Secure Remote Work: The rise of remote work increases the vulnerability of SaaS applications to attacks. SaaS security solutions provide secure remote access, protect data during transmission, and monitor user activities to ensure a secure remote work environment.
- Monitor User Activities: SaaS security solutions offer real-time monitoring of user activities within applications. This helps detect unusual behavior, unauthorized access, and potential security breaches, enabling quick response and remediation.
- Automate Security Processes: Automation is crucial for timely threat detection and response. SaaS security solutions offer automated alerts, incident response, and remediation actions, reducing the time required to address security incidents.
- Integrate with Ecosystem: SaaS security solutions can seamlessly integrate with other security tools, such as SIEMs, IAM solutions, and CASBs. This integration creates a unified security ecosystem that enhances threat detection and response.
- Adapt to Evolving Threats: Cyber threats evolve rapidly. SaaS security solutions stay updated with the latest threat intelligence, ensuring that your organization is equipped to defend against new and emerging threats.
- Maintain Business Continuity: A security breach can disrupt business operations and damage reputation. SaaS security solutions ensure business continuity by preventing downtime due to security incidents.
Exploring the Best SaaS Security Solutions
As the digital landscape evolves, security solutions emerge as crucial guardians of data integrity and user privacy. Within this realm, two primary categories stand out:
- Browser-Based Solutions: Browser-based security solutions take a proactive stance towards safeguarding your workforce’s browsing activities. These solutions not only monitor user interactions with SaaS applications but also assess associated risks.
- By enforcing a zero-trust approach, browser-based SaaS solutions control access to applications, authorize in-app actions, and customize user permissions. This dynamic approach extends to real-time monitoring and comprehensive user context, ensuring a holistic security approach.
- API-Based Solutions: API-based security solutions integrate seamlessly with diverse SaaS applications. However, they are limited to officially onboarded applications with API support and lack SaaS agnostic capabilities. API-based solutions excel with leading SaaS applications due to their robust API infrastructure and widespread usage.
It’s important to note that their effectiveness diminishes with applications lacking comprehensive API support. These solutions fall short in discovering and securing unsanctioned applications and lack the ability to contextualize policies based on user browser conditions.
| Platform | Category | Best Features | Most Suitable For |
| LayerX Security | Browser-based | Browser security platform for any browser, hassle-free deployment without affecting user experience. | Enterprises requiring extensive security features, especially with unsanctioned apps and unmanaged devices. |
| ManageEngine Browser Security Plus | Browser-based | Control Browser Components, Monitor Browser Health, Automated Vulnerability Management. | Enterprises aiming to shield data from browser-based threats. |
| ManageEngine Log360 | SIEM | Threat Intelligence Database, Visual Dashboard, Incident Management. | Enterprises tackling threats across on-premise, cloud, and hybrid environments. |
| NordLayer | Cloud-based | Multi-layered Security Approach for Safeguarding SaaS Apps in Networks. | Enterprises safeguarding cloud apps, users, and sensitive data. |
| Grip Security | Browser-based | All-in-One, User-Friendly Platform. | Organizations seeking a consolidated SaaS security control plane. |
| Talon | Browser-based | SaaS Security for Unmanaged Devices. | Enterprises enforcing strict SaaS access control on unmanaged devices. |
| Wing Security | API-based | Advanced Automation for Enhanced Security. | Businesses of all sizes seeking robust security for managed SaaS applications. |
| Authomize | API-based | Identity-Based Authorization & Security for Development and IT Applications. | Large R&D Departments in need of identity-based security for sanctioned applications. |
| DoControl | API-based | Code-Free SaaS DLP. | Enterprises sharing SaaS data and requiring code-free Data Loss Prevention solutions. |
Top 13 Saas Security Solutions of 2023:
Browser-based Solutions
1. LayerX
Renowned for its user-friendly interface and extensive array of immensely valuable SaaS security functionalities spanning diverse browser applications, including both approved and unapproved ones, LayerX stands out as a preeminent browser-agnostic security platform.
LayerX earns its distinction as an unparalleled solution dedicated to bolstering browser security. Its pivotal role lies in safeguarding applications, data, and devices against an array of online threats and vulnerabilities.
Given that browsers constitute an integral facet of virtually every business operation, a specialized browser security platform like LayerX becomes intrinsic to operational dynamics. The essence of LayerX’s competence lies in its vigilant oversight of SaaS-linked browsing events. This oversight facilitates the identification of all applications, users, and identities within the SaaS ecosystem. The platform extends its efficacy to scrutinize each user’s behavioral patterns and activities, curbing malicious app interactions and preempting data theft or leakage.
The uniqueness stems from its capacity to offer identical visibility and defense to all SaaS applications engaged by the corporate workforce. This encapsulates sanctioned, semi-sanctioned, federated sanctioned, and fully unsanctioned applications. This comprehensive approach secures the environment seamlessly, devoid of necessitating infrastructure changes or time-intensive configurations.
Salient Features:
- Real-time tracking of user activities.
- Prompt alerts for detecting risky behaviors.
- AI-powered session safeguarding.
- Robust tools for shielding against data exfiltration and theft, encompassing policy configuration for actions such as data submission, file downloads and uploads, and in-app activities.
Advantages:
- Effortless integration with diverse browsers.
- Uninterrupted monitoring coupled with automatic alerts.
- Adaptive browser modification to address assorted risks.
- Infuses user security context into SaaS security protocols.
Final Verdict: LayerX presents an optimal approach to SaaS security, marked by swift deployment and a robust suite of security attributes. Consequently, it emerges as a resounding recommendation for organizations seeking a robust SaaS security solution.
2. ManageEngine Browser Security
ManageEngine’s Browser Security Plus software offers an all-encompassing oversight and control over browser usage trends and components within your network. This enterprise-grade browser security solution is meticulously crafted to proactively thwart potential data breach scenarios by preemptively neutralizing threats such as viruses, ransomware, phishing attacks, and more.
The software excels in its inherent ability to autonomously identify vulnerabilities within browsers and adeptly manage them to avert any potential harm. Moreover, it provides the capability to configure and enforce security policies that serve as effective safeguards against a diverse array of cyber threats, shielding sensitive data from harm.
With the option to employ web isolation techniques, securely lock down enterprise browsers, and revoke access to popular web applications, you can substantially enhance the security of your data.
Salient Features:
- Effortlessly manage browser settings and extensions for optimized browsing experiences.
- Real-time monitoring ensures a smooth and secure online environment for all users.
- Detect and resolve browser vulnerabilities automatically, enhancing network defenses.
- Tailor security configurations to safeguard against online threats effectively.
Advantages:
- Swift setup minimizes disruptions and accelerates integration.
- Free for networks with under 25 computers, ensuring accessibility.
- Easily generate in-depth reports for insightful network analysis.
Final Verdict: ManageEngine Browser Security Plus is a robust enterprise security tool that stands as a formidable defense against browser-centric threats. Its compatibility spans across a wide spectrum of browsers, showcasing its efficacy in preempting cyber attacks before they manifest into harm.
3. ManageEngine Log360
Log360 emerges as an extensive security solution tailored for enterprises, equipping them to effectively combat threats and proactively mitigate risks. The software harnesses an up-to-date reservoir of threat intelligence, enabling the rapid identification and interception of external threats. Upon implementation, the software operates in a vigilant manner, promptly detecting and alerting users to instances of data leaks, unauthorized file sharing, and data exfiltration.
An exceptional aspect of the software is its intuitive visual dashboard, which furnishes users with actionable insights. Reports generated by the software offer a comprehensive snapshot for tracking, managing, and responding to threats with utmost efficiency. These reports adhere to pre-defined templates meticulously crafted to align with crucial regulatory standards.
Salient Features:
- The system offers seamless integration with Cloud Access Security Broker (CASB) and Data Loss Prevention (DLP) solutions, enabling comprehensive security coverage and data protection across the Active Directory environment.
- By integrating with CASB, the solution enhances the security of Active Directory by extending visibility and control over cloud applications and services that interact with the directory.
- The integration with DLP systems ensures that sensitive data within the Active Directory is safeguarded
- The system provides robust data visualization capabilities, presenting complex auditing and security data in a clear and easily understandable format.
- In the event of security incidents or anomalies, the solution offers proficient incident management features. It promptly alerts administrators about suspicious activities, unauthorized access, or policy violations, allowing them to take immediate corrective actions.
- The core feature of the solution is real-time auditing of the Active Directory that continuously monitors activities, changes, and access attempts, providing a real-time stream of events that helps detect and respond to security threats promptly.
- The system employs advanced algorithms to identify anomalous behavior within the Active Directory. This could include unusual login patterns, access from unfamiliar locations, or escalated privileges, triggering alerts for potential threats.
- Aministrators can configure customizable alerts based on specific events or thresholds. This feature ensures that critical activities are promptly brought to the attention of the security team.
Advantages
- Receive immediate alerts about potential security threats as they occur.
- Present complex security data in a user-friendly interface for easy understanding.
- Generate comprehensive reports that meet regulatory compliance requirements.
- Versatile compatibility to ensure seamless integration and functionality across diverse IT environments.
- Adapt to various systems, whether legacy or modern, for unified security management.
Final Verdict: With its capacity to provide real-time alerts for threats, reports in harmony with regulatory mandates, and a built-in repository of threat intelligence, Log360 stands as a formidable barrier against both internal and external threats.
4. NordLayer
With NordLayer, you gain access to a SaaS security solution renowned for its ability to fortify an extensive array of subscription-based business and collaboration applications such as SFDC, Microsoft 365, and Slack. Upon implementation, this tool extends its protective reach to encompass remote, local, and hybrid workforces.
NordLayer’s distinction lies in its remarkable provision of App Visibility and Control. This feature empowers IT administrators and security teams to attain enhanced control and visibility over network access by current users. Moreover, the tool facilitates access limitation to specific applications. You can expertly configure and deploy policies that exclusively authorize designated users to access SaaS apps.
Key Attributes:
- Identity and Access Management for comprehensive control over user identities and access privileges.
- Proactive Threat Prevention with advanced algorithms for early detection and mitigation of security threats.
- Cloud Access Security Brokers (CASB as an extension of security policies to cloud environments.
- Intuitive control panel for efficient management.
- Detailed reports for audits and regulatory compliance.
- Seamlessly operates across diverse IT environments.
- Real-time threat notifications for quick response to security breaches.
- User-friendly dashboard with visual snapshot of security status for informed decisions.
- Adapts to different OS, networks, and configurations.
Advantages:
- Exceptional Scalability helps effortlessly grow with the network, accommodating expansion.
- Augmented network visibility provides comprehensive insights into activities and user behaviors.
- Elevated automation capabilities to streamline tasks, enhances efficiency, and reduces manual work.
Final Verdict: NordLayer emerges as a compelling SaaS security solution adept at providing a protective shield for a diverse spectrum of applications. Its proficiency lies in bestowing users with amplified control and visibility over SaaS applications, complemented by the ability to configure access policies tailored to authorize or restrict user access to network apps.
5. Grip Security Solutions
Grip Security stands out as a premier provider of SaaS security solutions, offering a comprehensive SaaS Security Control Plane (SSCP) suite that empowers businesses to embrace a business-centric IT strategy while maintaining robust security.
The software boasts an array of unified visibility tools, workflow automation, analytics, permission control, and other essential features, cementing its reputation as a highly reliable security solution.
Established in 2021, Grip serves as an all-encompassing security platform, delivering extensive security coverage across all your applications, devices, and geographical locations. With a track record spanning over a decade, the platform equips you with the historical data needed for effective mapping and mitigation of SaaS-related risks.
Salient Features:
- Comprehensive SaaS visibility for deep insights into SaaS applications.
- Automates risk assessment and management processes.
- Strong authentication, secure credential storage, blinded password generation.
- Continuously analyzes, indexes, and validates SaaS data.
Advantages:
- A simplified and efficient process for implementing the solution.
- Customized policies tailored to security measures for specific needs, enhancing protection.
Final Verdict: Grip Security is a recommended choice for businesses of all sizes. They offer various training options, including documentation, live online sessions, and in-person training, complemented by round-the-clock online customer support services. The software’s user-friendliness and diverse feature set make it a valuable asset.
6. Talon

Talon emerges as a purpose-built browser tailored for enterprises, carving out a secure operational landscape. The software extends its protective umbrella over both managed and unmanaged devices within your business, transcending geographical boundaries, device types, and operating systems.
Endowing your business with flexibility and resilience, Talon stands as a contemporary, cost-effective platform, fortified by the endorsement of prominent cybersecurity investors such as Ballistic Ventures, Crowdstrike, Merlin Ventures, and Sorenson.
Talon’s implementation does not entail convoluted processes, streamlining your experience.
Salient Features:
- SQL Data Loss Prevention Tools that empower data protection through tools like file encryption and clipboard access restrictions, ensuring sensitive information remains secure.
- Comprehensive scanning to thoroughly scanning downloaded and uploaded files for potential threats, mitigating risks from malicious content.
- Providing in-depth monitoring of user actions to detect and address any suspicious or unauthorized activities.
- Browser Policy Management to enforce security measures, ensuring safe browsing experiences and safeguarding against potential threats.
- Assisting in forensic analysis by maintaining detailed records of user activities and interactions, aiding in investigations and incident response.
Advantages:
- Streamlined installation process that seamlessly configures remote systems.
- Works smoothly across Windows, Mac, Android, and iOS devices, ensuring versatility and accessibility.
Final Verdict: Talon boldly asserts the potential to slash Total Cost of Ownership (TCO) by up to 80%, fostering accelerated business growth. The platform boasts SOC 2 Type 2 certification and proudly bears the honor of being named the 2022 Gartner® Cool Vendor award winner for Hybrid Work Security.
7. Island Sec
Island Sec introduces an enterprise browser platform designed to seamlessly merge security and productivity within your business operations. With its open-source framework, Island functions akin to Chrome, ensuring familiarity and ease of use.
Functioning as a Zero Trust platform, Island Sec stands as a robust guardian, offering comprehensive data protection through governance, vigilant monitoring, and a suite of invaluable tools. This browser serves as a robust defense against phishing attempts and malicious websites, fortified by its anti-malware measures and isolation technology.
Key Features:
- Data Governance Empowerment helps establish and enforce data interaction policies for responsible handling.
- Attain 100% visibility into user actions and infrastructure for proactive threat management.
- Defend against malicious websites and phishing with robust security measures.
- Implement VDI for enhanced security, reduced maintenance burdens, and cost savings.
Advantages:
- By employing efficient data compression techniques and streamlined content delivery, users can access information with minimal delays, increasing productivity and satisfaction.
- The platform offers an intuitive and entirely native zero-trust experience for users. This means that the user interface and interactions are designed to seamlessly integrate with the user’s workflow while adhering to a zero-trust security model.
Final Verdict: Island Sec emerges as an immensely practical platform, garnering a resounding recommendation for businesses across the spectrum of sizes. Its user-friendliness stands complemented by its customizable nature, capable of aligning with your unique business requisites. This unified platform empowers you to oversee and manage user activities from a singular vantage point.
Cloud-based solutions:
8. Wing Security
Wing stands as a trailblazing cloud-based platform at the forefront of SaaS security. Esteemed with ISO 27001:2013 and AICPA SOC certifications, and adorned with the Global Infosec Award by Cyber Defense Magazine, it boasts a stellar pedigree.
This platform operates seamlessly through automated processes, encompassing app classification and authorization, persistent user activity monitoring, and adept management of potential vulnerabilities. The end result is an environment that seamlessly blends security and productivity.
Salient Features:
- The system performs an exhaustive analysis of permissions, data sharing, user activities, and more to uncover potential vulnerabilities.
- Advanced automation tools detect and address security concerns in real-time, preventing issues from escalating.
- Granular management allows for full control over apps, users, and files, ensuring compliance and data security.
- Ongoing surveillance of SaaS applications safeguards data integrity and user interactions.
Advantages:
- The system seamlessly integrates non-intrusive technology into your environment, ensuring that security measures do not disrupt the user experience or workflow.
- Through the utilization of cutting-edge algorithms, the system autonomously identifies and halts risky user sessions in real-time. This proactive approach helps prevent potential threats from escalating and minimizes the impact of security breaches.
Final Verdict: Wing Security’s advancement in automation is deserving of commendation. The platform is characterized by its simplicity, robustness, and user-friendliness. Coupled with continuous monitoring and analytical capabilities, it solidifies its status as a top-tier choice, aptly suitable for businesses of all sizes.
9. Authomize
Authomize emerges as a cloud-based SaaS security solutions provider, offering unparalleled access and insight into every facet of your business operations. This platform diligently observes and identifies all assets within each environment, meticulously monitors user activities, streamlines mass permission cleanups, and empowers you to establish policies that enable automation to safeguard crucial business information.
A hallmark of the platform is its seamless integration with your everyday applications such as Salesforce, Dropbox, Box, Google Cloud, and more.
Key Features:
- Advanced Risk Detection through a combination of sophisticated algorithms and real-time monitoring, it proactively identifies potential threats that might otherwise go unnoticed.
- Empowering you with the ability to establish and enforce security policies tailored to your organization’s unique needs, the system allows for refined control over access to vital business data.
- The integration of automated remediation tools enables the system to take predefined actions or corrective measures, reducing manual intervention and minimizing potential damage.
- Applications such as Okta, Box, Office 365, GitHub, Dropbox, and others are easily brought into the fold, ensuring that your security measures extend across your entire digital toolkit.
Advantages:
- Through offering a free trial, individuals and businesses can experience the software’s features, interface, and functionality without committing to a full purchase.
- The software is designed to ensure a smooth and seamless integration process with the platforms you already prefer and utilize. This integration eliminates the need for extensive adjustments to your workflow or disruptions to your existing setup, facilitating a more efficient adoption process.
Final Verdict: Authomize boasts an impressive roster of trusted partners including Fiverr, GitLab, Coinsource, NAU County, and others. It proudly garners recognition as one of the Top 100 Cybersecurity Startups by Cyber Defense Magazine, along with receiving Gartner Cool Vendor awards in 2021 and more. With these accolades and endorsements, Authomize stands as a highly recommended choice for businesses of all sizes.
10. DoControl
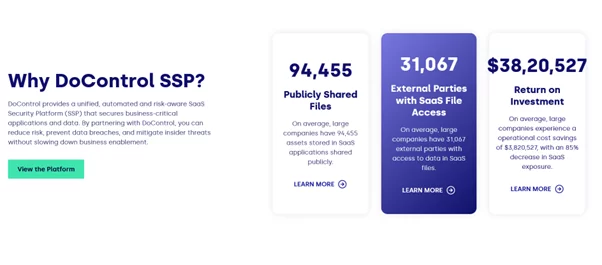
DoControl stands as a preeminent platform in the realm of SaaS security, dedicated to redefining Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) to fortify SaaS data security.
The platform’s offerings, encompassing SaaS asset management, continuous monitoring, and automated security workflow management tools, underscore its praiseworthy nature.
Salient Features:
- The software offers robust real-time scanning capabilities to continuously monitor data flows within your system. It includes advanced data classification tools that can identify and label sensitive information, such as personal identifiable information (PII) and confidential documents.
- Recognizing that different organizations have varying security needs, the software provides workflow customization options like rules for data access, sharing, and handling, helping you proactively safeguard sensitive data and prevent unauthorized access.
- To address the threat of insider risks, the software incorporates features that can detect inappropriate user behavior.
- The software maintains comprehensive audit trails that document all activities performed by end-users.
- Automating security and compliance tasks is a crucial aspect of managing complex IT environments. The software includes automation tools that can take immediate action when non-compliant SaaS activities or permissions are detected.
Advantages:
- It seamlessly integraties with a diverse range of popular applications. This integration extends to well-known platforms such as Microsoft Teams, Okta, Dropbox, Google Drive, OneDrive, Slack, BambooHR, and many others. This ensures that the software can seamlessly fit into your existing technology stack, minimizing disruptions and enhancing user adoption.
- The software comes with a strong endorsement of security through its ISO 27001, SOC2 Type II, and CSA CAIQ certifications. The ISO 27001 certification signifies the adherence to globally recognized standards for information security management systems, ensuring that the software’s security practices.
Final Verdict: DoControl stands as a dependable bastion for data security. This cloud-based solution proficiently shields against a diverse array of risks, ranging from insider threats to those posed by third-party applications.
As an ISO 27001-certified platform, DoControl not only elevates efficiency but also bolsters security for businesses. Renowned security entities such as CrowdStrike, KKR, IronNet, and others repose their trust in DoControl for cutting-edge cloud-based SaaS security solutions.
11. Varonis
Established in 2005, Varonis stands as a venerable and esteemed platform renowned for its cloud-based SaaS security solutions. The platform boasts an illustrious clientele that includes prominent names like Nasdaq, Toyota, Coca-Cola, Loreal, Harvard University, among many others.
Varonis extends its services across diverse industries, spanning Finance, Healthcare, Federal Government, Education, Manufacturing, and State & Local Government.
Salient Features:
- Gain insights and control over both cloud and on-premises data, making informed decisions about security.
- Swiftly respond to data breaches with automation tools for identification, containment, and mitigation.
- Set policy control measures to preempt unauthorized data access and leaks.
- Automate data movement, archiving, and deletion based on conditions, ensuring compliance.
- Detect security threats early by analyzing user behavior patterns using Machine Learning.
Advantages:
- The software provides strong file encryption and lockdown capabilities, ensuring the security and confidentiality of sensitive data.
- The software seamlessly integrates with a range of prominent applications, including Zoom, Okta, Slack, Salesforce, and more.
Final Verdict: Varonis emerges as a formidable security fortress, ensuring the protection of sensitive data both in the cloud and on-premises. It acts as a safeguard against insider threats and cyber attacks, enhancing your business’s security posture.
Varonis boasts an impressive spectrum of features. With ISO 27001, 27017, 27018, and 27701 certifications, you can have full confidence in the security of your personal data.
12. Adaptive Shield

At the forefront of SaaS security, Adaptive Shield stands as a renowned platform esteemed for its automation prowess in step-by-step remediation. The platform’s impact and innovation have earned it notable features in esteemed publications such as Forbes, Bloomberg, TechCrunch, and SecurityWeek. Furthermore, it garners backing from notable names including Insight Partners, Okta Ventures, and Vertex Ventures.
Distinguishing itself as an innovative powerhouse, Adaptive Shield proudly upholds ISO 27001 compliance and GDPR compliance. The platform’s repertoire of in-depth security checks and its automated remediation capabilities truly stand out.
Key Features:
- Vigilant monitoring of SaaS applications connected to your business, maintaining a watchful eye on their activities and interactions.
- It bestows comprehensive visibility into user accounts, activities, and permissions within the SaaS environment, enhancing your control over data access.
- The system conducts thorough and meticulous security checks, evaluating potential vulnerabilities and risks across the SaaS landscape.
- Leveraging automation tools, the software enables systematic step-by-step remediation actions, allowing for efficient responses to security concerns.
Advantages:
- The software offers seamless integration with an extensive array of platforms, including Slack, BambooHR, Asana, GitHub, Dropbox, Jira, Microsoft 365, Okta, Trello, and many others.
- The solution facilitates comprehensive control over all connected applications, empowering you to manage and enforce security policies consistently across various platforms.
Final Verdict: Adaptive Shield secures its status as a trusted and widely embraced cloud-based SaaS security platform. Being honored with the ‘Cool Vendor’ recognition by Gartner in 2022 and awarded the ‘Top 10 Baby Black Unicorn’ distinction by Cyber Defense Magazine in 2021, it has earned its place of distinction.
13. Torii
Torii, a dynamic cloud-based SaaS security solution, reigns supreme with its arsenal of advanced detection and monitoring tools. It not only facilitates real-time monitoring of app usage but also streamlines automated offboarding and onboarding processes, ultimately reducing operational costs. Furthermore, Torii empowers you to maintain a vigilant watch over every app within your operational environment.
This platform’s excellence has not gone unnoticed, as evidenced by its recent accolades including ‘High Performer,’ ‘Best Usability,’ ‘Momentum Leader,’ and ‘Best Relationship’ from G2.com.
Key Features:
- Through predefined workflows and integration with user management systems, the system automates the provisioning and deprovisioning of access rights and permissions.
- The system employs advanced endpoint detection tools which ensures that any potential threats or vulnerabilities are promptly identified and addressed, reducing the risk of security breaches and data leaks.
- By conducting a thorough analysis of the applications used within your organization, the system identifies redundant or underutilized software subscriptions.
Advantages:
- Whether it’s financial management with QuickBooks, streamlined communication through Slack, collaboration with G Suite, identity management via Okta, virtual meetings using Zoom, or web browsing with Mozilla, this software effortlessly fits into your existing technology ecosystem.
- Holding a SOC 2 Type II certification is a testament to its commitment to stringent security practices. Additionally, the software’s compliance with the General Data Protection Regulation (GDPR) underscores its dedication to protecting user data and respecting privacy rights.
Final Verdict: Torrii enjoys the trust of globally renowned and reputable enterprises such as Bumble, Payoneer, Fiverr, among others. Glowing testimonials from satisfied users highlight its excellence. The platform’s adeptness at saving time and costs makes it a sterling recommendation for businesses of all sizes.
Pricing: For personalized pricing details, direct engagement with the provider is recommended.
Conclusion:
The landscape of SaaS applications is expanding at an exponential pace, redefining the contours of modern business operations. However, this digital transformation has also illuminated the potential security fissures that demand prompt attention. In light of these realities, the adoption of robust SaaS security solutions is not just an option; it’s an intrinsic necessity to fortify the digital infrastructure against the relentless tide of cyber threats. By investing in cutting-edge security technologies, organizations can navigate the SaaS landscape with confidence, safeguard their sensitive data, and elevate their cybersecurity posture in an ever-evolving digital milieu.
FAQs on SaaS Security Platforms:
How do SaaS security platforms work?
SaaS Security Platforms work by providing a range of security measures such as identity and access management, encryption, threat detection, behavioral analytics, and policy enforcement. These tools collectively safeguard user access, monitor activities, and detect anomalies in SaaS applications.
What features do SaaS security platforms typically offer?
SaaS Security Platforms offer features like user authentication, single sign-on (SSO), multi-factor authentication (MFA), data encryption, access controls, real-time monitoring, threat detection, automated remediation, and integration with other security tools.
Can SaaS security platforms secure both managed and unmanaged devices?
Yes, many SaaS Security Platforms offer solutions to secure both managed and unmanaged devices. These platforms enable organizations to enforce security policies, monitor activities, and detect threats on various devices, ensuring a consistent level of protection.
Can SaaS Security Platforms Be Integrated with Other Security Solutions?
Yes, SaaS Security Platforms can be integrated with other security solutions such as Security Information and Event Management (SIEM) systems, Identity and Access Management (IAM) solutions, and Cloud Access Security Brokers (CASBs) to create a comprehensive security ecosystem.



