Did you know that the digital landscape is under constant siege? A staggering statistic reveals that a mind-boggling 30,000 websites fall victim to cyberattacks every single day. This alarming figure underscores the pervasive and relentless nature of online threats that loom over businesses, organizations, and individuals alike.
As the digital realm becomes increasingly integral to our lives, ensuring the security of your website is paramount. Neglecting this essential aspect is akin to leaving the front door of your site wide open to malicious actors. The consequences of such negligence can be catastrophic, encompassing data breaches, website crashes, and financial losses.
Consider the words of renowned cybersecurity expert, Bruce Schneier, who aptly stated, “The only truly secure system is one that is powered off, cast in a block of concrete, and sealed in a lead-lined room with armed guards.” While this statement may sound extreme, it highlights the seriousness of the online security landscape.
In this digital age, the responsibility to protect your website cannot be overstated. Implementing robust security measures is not merely an option; it’s an imperative safeguard against the ever-present threat of cyberattacks. Your website’s integrity, data, and financial stability depend on it. Don’t wait until it’s too late – fortify your online presence today.
Understanding Website Hacking: Signs and Prevention

Before delving into strategies for safeguarding your website against hacking, it’s essential to recognize the indicators of a compromised site.
While the aftermath of a website hack can vary, certain patterns commonly emerge. If your website has fallen victim to hacking, unmistakable signs will manifest. Here are some prevalent manifestations of hacking:
1. Ransomware: Hackers threaten to expose your data or deny access to your site unless a ransom is paid.
2. Gibberish Hack: Numerous auto-generated pages with keywords and nonsensical content appear, designed to boost their Google ranking. Clicking on these pages often leads to malicious websites.
3. Cloaked Keywords Hack: Similar to the gibberish hack, but more sophisticated. These pages may initially resemble your site’s pages, with only the written content altered.
4. Japanese Keywords Hack: Random pages in Japanese are created and packed with affiliate links to counterfeit merchandise stores.
5. Malicious code/Viruses: Insertion of malicious code or viruses can lead to site downtime or restricted access. This may also impact your hardware.
6. Denial of Service (DoS): Hackers employ bots to flood your website with requests, overwhelming the server and causing it to crash.
7. Phishing: Scammers impersonate your business, using your branding to contact clients and collect personal information.
When selecting a hosting provider, like Nestify, for your website built on a content management system such as WordPress.org, consider the following options for securing your site:
- Opt for a hosting provider with a free SSL with all plans, ensuring your website’s basic security.
- Alternatively, you can install a basic Let’s Encrypt SSL at no cost.
- You may invest in an advanced SSL certificate for enhanced security. These certificates are available at varying prices and can be purchased from hosting providers or domain registrars. The free SSL version should suffice for most websites unless you operate a large-scale online store or manage extensive sensitive data.
Strategies to Ensure Website Security:
1. Securing Your Website: The Importance of SSL Certificates
One of the simplest yet crucial steps to safeguard your website, your online presence, and the privacy of your users is by installing an SSL (Secure Sockets Layer) certificate. You may not realize it, but SSL is ubiquitous on the web, recognizable by the “s” in “https” and the padlock symbol in the address bar.
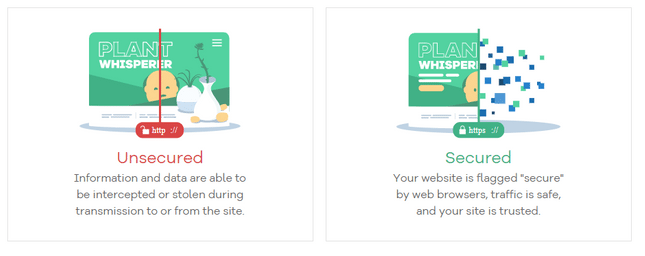
SSL, or Secure Sockets Layer, is a protective shield for your website. By installing an SSL certificate, you encrypt data between your site and its visitors, including login information. Various levels of SSL exist, with advanced versions essential for e-commerce websites handling payment data.
Why is SSL so vital? Google now flags websites without SSL, cautioning visitors and affecting their search ranking. This security measure is especially critical if your website involves payment processing, requires user login credentials, or transfers files. Without SSL, sensitive data is exposed and susceptible to hackers.
An SSL certificate is necessary if you run an eCommerce store or collect visitor information, like emails, on your site. In addition to boosting SEO, SSL certificates prove that any data visitors send to your site uses an encrypted channel, so hackers can’t see it while it’s in transit.
You don’t need to delve into the technical intricacies of SSL; what’s essential is understanding that your website requires it and knowing how to obtain it.
There are several methods to implement SSL:
1. Choose a reputable website builder with free SSL as a standard feature.
2. Opt for a hosting provider like HostGator, which offers free SSL with all plans, especially if using a content management system like WordPress.org.
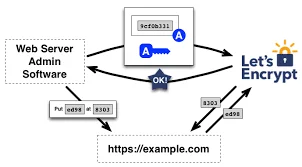
3. Install a basic Let’s Encrypt SSL independently, without cost.
For enhanced security, you may invest in an advanced SSL certificate. Prices vary; these certificates can be obtained from hosting providers or domain registrars. However, for most websites, the free SSL version should suffice unless you manage a large-scale online store or handle extensive sensitive data.
2. Enhance Your Website’s Security with Anti-Malware Software
The term “anti-malware software” might sound complex, but the good news is that it takes care of the technical complexities, leaving you with peace of mind. Numerous anti-malware solutions are available, offering a range of options. Some come with free plans, like Bitdefender Antivirus Free, while others require a paid subscription, such as SiteLock.
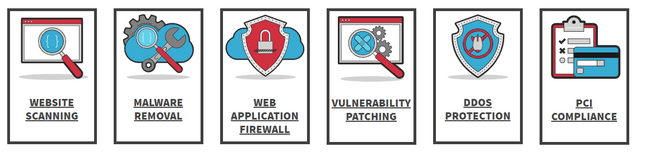
SiteLock, trusted by over 12 million websites, offers various packages with different levels of protection. This allows you to customize your security based on your site’s requirements and budget. Some of the security services it provides encompass:
- Web scanning
- Malware detection and removal
- Web application firewall
- Vulnerability patching
- DDoS protection
- PCI compliance
If these terms seem unfamiliar, don’t worry – that’s precisely what anti-malware software is designed to handle!
A reliable website builder or hosting provider should ensure your site’s security. Many hosting providers include anti-malware software in their plans, with some even offering premium services like SiteLock for free.
Others provide a built-in security suite, as seen with InMotion, which includes:
- Free SSL
- Hack protection
- Automatic backups
- DDoS protection
These fundamental security features should be a priority when selecting a hosting provider. Whether your provider includes these tools or offers extensions like SiteLock, anti-malware software protects your website. Web hosts are the backbone of your website. They help you establish an online presence and offer essential tools to shape your website’s appearance and functionality. Quality hosting providers implement security protocols, including automatic security patches and updates, to safeguard the content management systems they host, such as WordPress. Maintaining server security and implementing crucial security monitoring is the hosting provider’s responsibility.”
3. Strengthen Your Passwords for Maximum Security

Passwords, those seemingly mundane strings of characters, hold a vital role we sometimes underestimate. Your password often serves as the sole barrier between a hacker and your precious personal information.
The good news is that enhancing password security is critical and one of the simplest steps you can take to fortify your website’s defenses. Just invest 20 minutes today in fortifying your passwords, and you’ll significantly enhance your site’s security.
Consider this eye-opening fact: A survey found that 40% of small businesses fell victim to cyberattacks due to compromised employee passwords, costing an average of over $380,000 per attack!
The UK’s National Cyber Security Center surveyed globally the most frequently breached passwords. They compiled a list of the top 10 most hacked passwords. If you’re using any of these, it’s high time for a change (like, right now!):
- 123456
- 123456789
- qwerty
- password
- 111111
- 12345678
- abc123
- 1234567
- password1
- 12345
Instead of opting for easily guessable phrases, consider these alternatives:
- Combine three unrelated yet memorable phrases.
- Use a randomly generated sequence of characters.
- Avoid password reuse by utilizing a password manager to keep track of them.
- Make your password lengthy.
- Never incorporate personal information, as it’s usually the first target of hackers!
Many password tips exist, so feel free to combine several tactics to craft virtually uncrackable passwords. Once you’ve created robust passwords, handle them with care. Avoid sharing them, even with friends, and remember to change them regularly, ideally about once every quarter. Your website’s security will thank you.
4. Maintain Your Website’s Software: Stay Updated for Security
We’re not referring to sharing the latest news or showcasing your newest products to your visitors. This is all about the crucial task of keeping your website’s software up to date. If you’re using a website builder, this responsibility is often managed for you, as most builders handle software updates and security matters. However, if your platform is WordPress, being proactive and timely with updates is essential.
You must keep the WordPress core software updated, along with any plugins you’ve integrated. Neglecting these updates can render your website outdated and susceptible to bugs, glitches, and, most concerning, malicious hackers armed with harmful code.
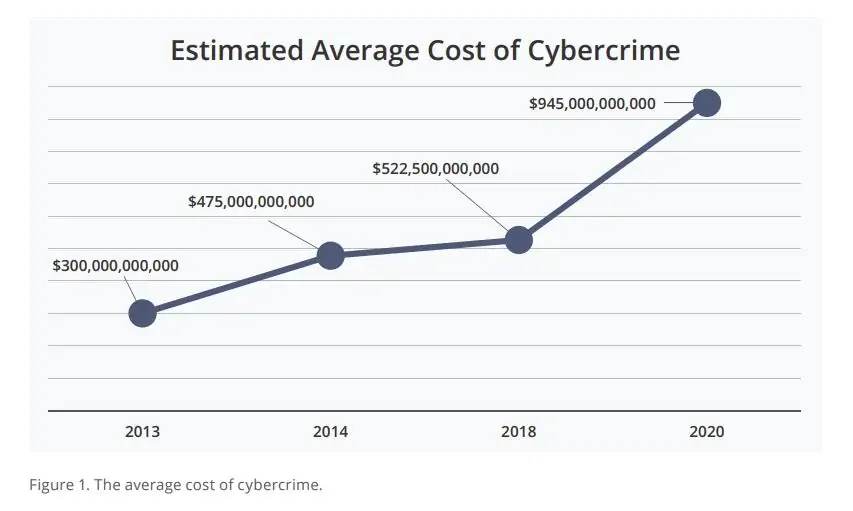
Did you know? Cybercrime is projected to cost the world $10.5 trillion annually by 2025!
You can typically configure these updates to occur automatically through your dashboard. Nonetheless, it’s wise to check and ensure everything runs smoothly periodically. Allowing your site to languish in an outdated state can pose severe security risks, so remaining vigilant about updates is a worthwhile practice.
It’s important to note that when selecting plugins for your WordPress site, exercise caution regarding their quality. Anyone can develop plugins, and low-quality ones may contain bugs or malicious code. Read reviews, seek out reputable developers, and thoroughly inspect plugins before clicking that “Install” button. Your website’s security depends on it.
5. Guard Against Assisting Hackers: Prioritize Online Vigilance
We understand that this is an obvious point. After all, who willingly hands over their details and invites their website to be hacked? That’s precisely why you’re reading this article, right? However, the reality is that people often unintentionally fall victim to scams and unknowingly divulge vital personal information.
Did you know that a staggering 92.4% of malware finds its way into systems through email? This makes email the primary method of attack, necessitating constant vigilance when checking your inbox for anything out of the ordinary.
While implementing advanced tech safeguards for your website is crucial, it’s vital to recognize that 95% of cybersecurity breaches result from human error. Safeguard your website by staying vigilant and maintaining a healthy suspicion of texts, emails, or phone calls requesting personal information.
Although it may sound straightforward, scams continue to evolve in sophistication. Here are five essential steps to ensure your website remains impervious to unwelcome intruders:
1. Exercise caution when using public or open internet connections, especially in shared spaces like cafes, as they lack security.
2. Never click on suspicious links in emails; instead, promptly delete such emails. Whether you’re using a professional email connected to your website or a personal one, this holds true.
3. Be meticulous about granting access to your website; verify that administrators are trustworthy individuals who prioritize security.
4. Immediately change your site’s default settings, passwords, and usernames after setting up your account. This is especially vital for WordPress websites.
5. Entrust access to your site only to verified professionals. Beware of scammers who may feign technical issues to gain control of your screen.
These practices seem like common sense, but staying on high alert is essential, mainly as phishing emails grow increasingly convincing. Your website’s security hinges on your vigilance.
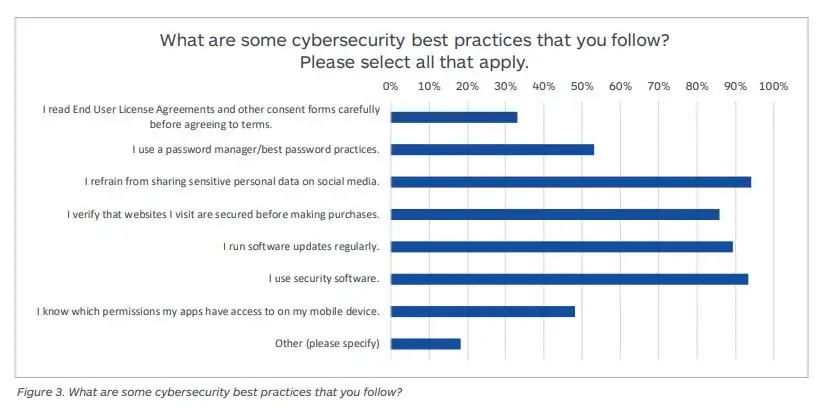
Source: The Blinding Effect of Security Hubris on Data Privacy by Malwarebytes 2019
6. Exercise Manual Control Over On-Site Comments
Is there a more satisfying moment than hitting that “publish” button on your website and witnessing comments start to flow in? It’s tangible evidence that people have visited your site and appreciated its content.
Comments serve as the perfect gauge of engagement, offer social validation to other visitors, foster connections within your niche, and even provide an avenue for constructive feedback. We cherish receiving comments, and so should you!
However, amidst the enjoyable comments lurk those that are less pleasant. Bots, fake profiles, and trolls stand ready to drop silly remarks or spammy links. It’s an annoyance; at worst, it poses a security threat to you and your users.
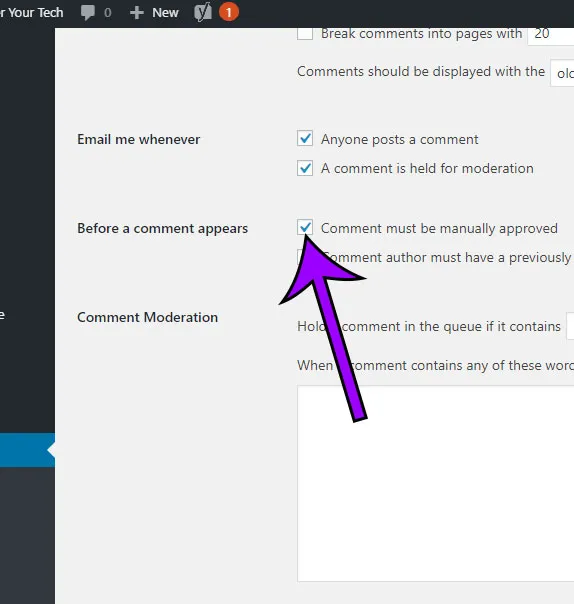
When people can post comments directly on your website, there’s a risk of malicious links slipping into the comments section. This can be particularly perilous for your website’s visitors, who may inadvertently click on such links, potentially exposing personal data or installing malware.
To combat this, you can adjust your website’s settings so that comments must be manually approved before appearing on your site. This allows you to weed out any spam. Other methods to mitigate the risk of malicious links include:
1. Employing anti-spam software or plugins (like Akismet for WordPress users).
2. Requesting visitors to register before they can comment.
3. Disabling comments on posts after a month or two.
By implementing these strategies, you can maintain a comments section that’s safe, enjoyable, and welcoming for both you and your visitors while keeping hackers and their malicious links at bay.
7. Maintain Regular Website Backups
Following the steps we’ve previously outlined will go a long way in thwarting hackers. However, never assume your site’s security is foolproof. Much like having a safety net while walking a tightrope, running routine backups of your website is a prudent measure.
Creating backups of your website guarantees that in the event of a catastrophe, you’ll still have a recent, intact version of your site safely stored and ready for relaunch.
A backup is a duplicate of your website data, encompassing files, content, media, and databases. A substantial backup storage capacity is essential for larger or more complex websites to accommodate all your data.
If your business website falls victim to hacking, you need a swift way to recover and resume operations to avoid losing customers. Utilize an automatic site backup service like CodeGuard, enabling you to swiftly restore your site’s most recent, untarnished version if anything goes awry. Ensure the service you select conducts daily backups, eliminating the need to revert to an outdated site version in case of a crash.
Now, how can you go about backing up your site to maintain seamless operations? There are various methods for backing up your website, including:
1. Utilizing a backup service such as CodeGuard or Sucuri handles the process for you at a cost.
2. Opt for a web host with backup features in its plans, like A2 Hosting. Some hosts come with built-in backup software or offer it as an add-on. However, these options may have limited storage capacity, so it’s advisable to only rely on them for some of your backup needs.
3. Employing a WordPress plugin like UpdraftPlus or VaultPress. WordPress users can conveniently install their chosen plugin and customize their backup preferences independently.
9. Defend Your Website Against Cross-Site Scripting (XSS) and Injection Attacks
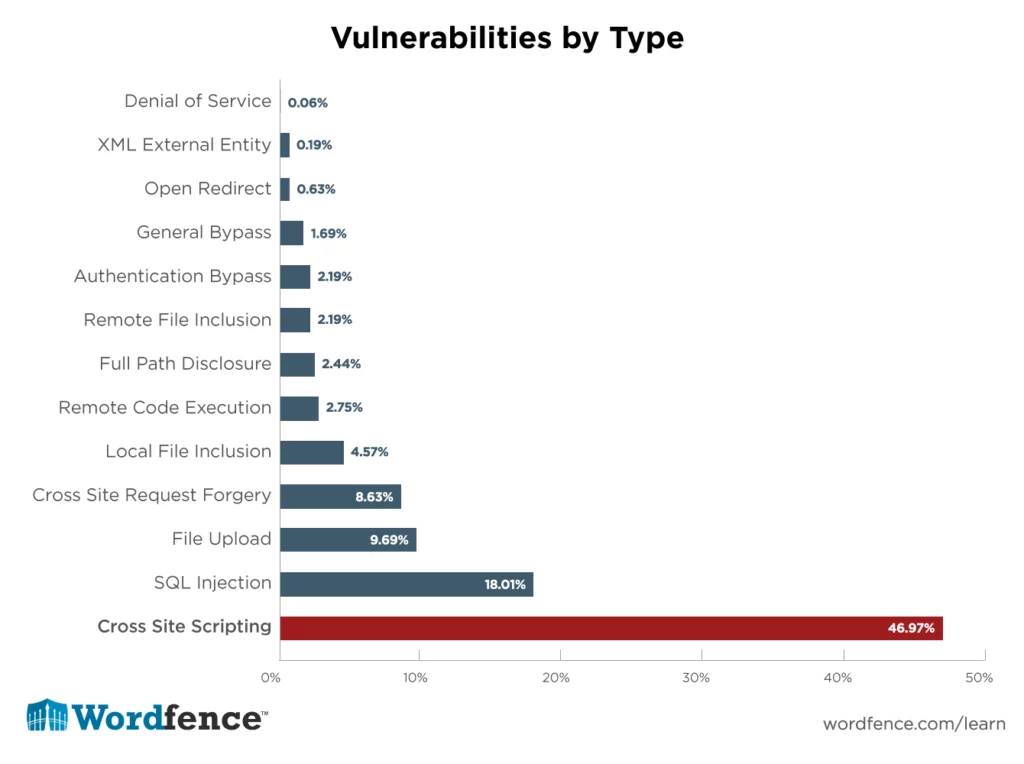
Cross-site scripting (XSS) represents a vulnerability that enables attackers to compromise user interactions within a vulnerable application. Typically, XSS vulnerabilities empower hackers to impersonate users, assume their identity, perform actions on their behalf, and access their sensitive data.
This attack becomes particularly concerning if the user possesses administrative privileges on your website. The attacker might replicate these powers in such cases, gaining complete control over the website’s functions and data.
XSS attacks unfold as follows: Manipulating a vulnerable website leads it to transmit malicious JavaScript to users. Once executed in the user’s browser, this script grants the hacker full access to the user’s interactions with the website.
There are three primary types of XSS attacks:
1. Reflected XSS: Malicious script originates from the current HTTP request.
2. Stored XSS: Malicious script arises from the website’s database.
3. DOM-based XSS: The vulnerability resides in client-side rather than server-side code.
Injection attacks, on the other hand, enable hackers to inject code into a program or query or insert malware into a computer, thereby executing remote commands.
The severity of these attacks hinges on the application’s nature and the breached user’s privileges. For instance, websites harboring vast data repositories or users with full administrative controls could suffer catastrophic consequences.
To fortify your defenses against XSS and injection attacks, adhere to these measures:
1. Encode data before presenting it to users.
2. Scrutinize and validate input upon its arrival.
3. Implement prepared statements or employ parameterized queries for database interactions.
4. Deploy Web Application Firewalls (WAFs) for Enhanced Security
5. A Web Application Firewall (WAF) is crucial in safeguarding websites by monitoring and filtering HTTP traffic between the website and the broader internet.
6. Typically integrated into a suite of security tools, a WAF offers robust cybersecurity. While it may not provide comprehensive protection against all attacks, it excels at thwarting cross-site forgery, XSS (Cross-Site Scripting), file inclusions, and SQL injections.
7. Imagine a WAF as a protective shield positioned before the web application. It is a barrier that users must pass through before gaining access to the website, thus shielding the server from potential threats.
8. WAFs typically operate using one of three methods: blocklist, allowlist, or combination. A blocklist blocks known attacks, while an allowlist exclusively permits pre-approved traffic.
9. When implementing a WAF, there are several factors to consider. Network-based WAFs, for instance, are locally installed to minimize latency. However, they are the costliest option and demand substantial storage resources.
10. Alternatively, a host-based WAF is integrated directly into an application’s software. This option is more cost-effective and offers greater customization. Nonetheless, it requires extensive ongoing maintenance.
11. Cloud-based WAFs provide an affordable and easy-to-implement solution. Users pay an initial fee and a monthly subscription to a third-party provider.
12. Your choice should align with your specific needs and priorities, so carefully assess the advantages and disadvantages of each option to identify the ideal solution for your circumstances.
Case Studies: Cybersecurity Breaches:
#1. The Twitter Bitcoin Phishing Scam: A Lesson in Cybersecurity Vigilance

In 2020, Twitter faced a monumental cybersecurity challenge when its employees fell victim to a cunning phishing scam.
Hackers successfully infiltrated 130 corporate Twitter accounts, each boasting a following of at least one million users. These weren’t just accounts; they included high-profile personalities and organizations such as Barack Obama, Elon Musk, Apple, and Uber.
The audacious hackers exploited this breach by employing 45 compromised accounts to perpetrate a Bitcoin scam. Shockingly, Twitter users collectively transferred approximately $180,000 in Bitcoin to the scammers’ accounts. As a consequence of this attack, Twitter’s stock price plummeted by 4%, illustrating the far-reaching consequences of cybersecurity breaches.
What sets this incident apart is that it exemplifies an insider threat—a scenario in which individuals within the organization unwittingly become conduits for cyberattacks. The attackers astutely capitalized on the fact that Twitter employees were working remotely due to prevailing circumstances, providing the perfect cover for their subterfuge. The hackers impersonated the Twitter IT department and contacted unsuspecting employees, ultimately gaining access to their accounts.
With these compromised staff accounts in their control, the hackers escalated their intrusion, obtaining administrator privileges. This allowed them to reset critical Twitter accounts and disseminate the fraudulent Bitcoin promotion across the platform.
This case underscores the vital importance of rigorous staff training in cybersecurity practices. It is a stark reminder that even the most prominent organizations can fall prey to cyber threats. To fortify defenses against such incidents, comprehensive cybersecurity awareness and training programs are imperative.
2. Microsoft: A tale of tycoon being pested with cyber threats

In a stark reminder of the pervasive cybersecurity threats faced by even the tech giants, Microsoft, the powerhouse behind the email systems of numerous global organizations, encountered a severe cyber onslaught in 2021. This attack targeted Microsoft’s email servers and exploited four distinct vulnerabilities.
These audacious hackers astutely pinpointed four zero-day vulnerabilities that had remained undetected by the server and its security services, affording them unrestricted access to the entire server infrastructure.
Within this breach, the attackers engaged in a multifaceted assault, accessing sensitive data, introducing ransomware into the ecosystem, and stealthily deploying backdoors that were exceedingly difficult to trace. This incursion’s sheer sophistication and scope made it a formidable challenge for Microsoft to mitigate.
This incident is a poignant reminder that even tech titans like Microsoft are susceptible to cyberattacks. It underscores the urgent need for organizations to fortify their cybersecurity defenses regardless of their size or prominence.
In a striking illustration of the magnitude of cyberattacks, 2022 bore witness to one of the most conspicuous incidents in the realm of cybersecurity.
3. Costa Rica: Blunder beyond repairs
The Costa Rican Government found itself in the crosshairs of a colossal cyber onslaught that profoundly impacted various facets of the nation. This extensive attack reverberated across critical sectors, including the finance ministry, government institutions, and private import-export enterprises. So significant was the breach that it prompted an unprecedented response – the Costa Rican government’s declaration of a national emergency in response to a cybersecurity incident.
The audacious hackers behind this attack brazenly issued a ransom demand of $20 million, underlining the stark reality that vulnerabilities in cybersecurity can exact an exorbitant toll. This incident serves as a stark reminder that the consequences of cyberattacks extend far beyond the digital realm, potentially posing severe disruptions to a nation’s economic and administrative fabric.
Conclusion:
Website security is not a one-time task but an ongoing process that demands constant vigilance and adaptation to evolving threats. In today’s digital landscape, where cyberattacks are becoming increasingly sophisticated, ensuring the security of your website is a critical aspect of maintaining your online presence and safeguarding the trust of your users.
By regularly updating your software, conducting security audits and testing, implementing access controls and authentication measures, educating your users, and being prepared for security incidents, you can significantly reduce the risk of security incidents and protect both your website and your users from harm. Remember that investing in website security is an investment in the long-term success and reputation of your online presence.
FAQs on Website Security:
How can I educate my website users about security best practices?
You can educate users through blog posts, email newsletters, and informational pages on your website. Additionally, consider providing resources on safe browsing and recognizing phishing attempts.
What should I do if my website experiences a security breach?
Refer to your incident response plan immediately. Isolate affected systems, investigate the breach, and take steps to mitigate the damage. Notify affected parties and report the incident to the appropriate authorities if necessary.



