In today’s digital landscape, where data is the lifeblood of businesses, ensuring robust security measures for cloud infrastructure has become imperative. As more organizations migrate to the cloud, it becomes essential to implement effective security solutions to protect sensitive information from cyber threats. Vultr, a leading cloud infrastructure provider, offers a powerful tool called Vultr Bare Metal’s Firewall that can augment the security of your cloud environment. In this blog post, we will explore the features and benefits of Vultr Bare Metal’s Firewall and provide practical tips on how to effectively utilize this solution to protect your cloud infrastructure.
Understanding Vultr Bare Metal’s Firewall
Vultr Bare Metal’s Firewall is a security feature provided by Vultr that allows users to define and enforce network access rules for their cloud infrastructure. It acts as a virtual barrier, inspecting and filtering incoming and outgoing traffic based on predefined rules.
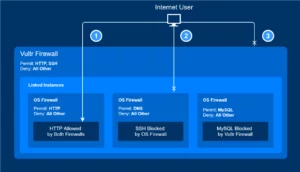
Key Features and Capabilities of Vultr Bare Metal’s Firewall
Vultr Bare Metal’s Firewall offers several key features, including:
- Access Control: Vultr Bare Metal’s Firewall provides you with the ability to establish and enforce access controls for your cloud infrastructure. You have the freedom to specify the permitted IP addresses or IP ranges that can access your resources, effectively limiting unauthorized access. This powerful feature ensures that only authorized entities can interact with your cloud environment, bolstering the security of your infrastructure.
- Port-Based Filtering: With Vultr Bare Metal’s Firewall, you can establish rules to allow or block specific ports for inbound and outbound connections. This incredible feature enables you to control which services are accessible to external entities and helps minimize the attack surface.
- Custom Rule Creation: The firewall offers the versatility to personalize firewall rules according to your specific needs. You have the control to specify protocols, ports, and IP ranges, enabling you to permit or restrict traffic based on your security policies. This level of customization empowers you to adapt the firewall rules to align with the distinctive characteristics of your cloud environment.
- Network Traffic Logging: Vultr Bare Metal’s Firewall logs network traffic, allowing you to monitor and analyze incoming and outgoing activity. The logs provide insights into attempted connections, blocked traffic, and potential security incidents. By reviewing these logs, you can identify suspicious patterns and take appropriate action.
- Rule Prioritization: The firewall allows you to set priorities for firewall rules, determining the order in which they are evaluated. This feature ensures that rules are enforced correctly and avoids conflicts or unintended consequences.
- Scalability: Vultr Bare Metal’s Firewall is designed to scale tremendously and effortlessly as your cloud infrastructure grows. Whether you have a small-scale setup or a large enterprise deployment, the firewall can handle increasing traffic volume and adapt to evolving security requirements without compromising on performance.
- Ease of Management: The intuitive interface of Vultr Bare Metal’s Firewall makes it easy to configure and manage your security policies. You can enable or disable firewall rules, create and modify custom rules, and adjust settings according to your changing needs. The user-friendly control panel simplifies the management of your cloud security.
- Integration with Other Security Measures: Vultr Bare Metal’s Firewall can work in conjunction with other security measures, like secure sockets layer (SSL)/transport layer security (TLS) certificates, intrusion detection and prevention systems (IDPS), and access control mechanisms. This integration enhances the overall security posture of your cloud infrastructure.
Benefits of Using Vultr Bare Metal’s Firewall
By leveraging Vultr Bare Metal’s Firewall, you gain the following benefits:
- Enhanced security: The firewall establishes a protective layer, preventing unauthorized access and mitigating potential attacks.
- Granular control: You can concrete precise rules to control incoming and outgoing traffic, reducing the attack surface.
- Simplified management: The intuitive interface of Vultr Bare Metal’s Firewall makes it easy to configure and manage security policies.
- Scalability: The solution scales seamlessly as your cloud infrastructure grows, ensuring consistent protection.
Configuring Vultr Bare Metal’s Firewall
-
Accessing the Vultr Control Panel
To configure Vultr Bare Metal’s Firewall, log in to your Vultr account and navigate to the Vultr Control Panel.
-
Enabling and Disabling Firewall Rules
Within the Control Panel, you can enable or disable firewall rules as per your requirements. This allows you to modify access permissions swiftly.
-
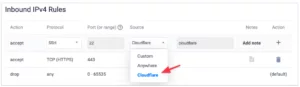
Creating Custom Firewall Rules
Vultr Bare Metal’s Firewall provides the option to create custom firewall rules. This feature enables you to define specific protocols, ports, and IP ranges for greater control over network traffic.
-
Managing Inbound and Outbound Traffic
With Vultr Bare Metal’s Firewall, you can manage both inbound and outbound traffic effectively. You can create your rules to allow or block traffic based on source and destination IP addresses, ports, and protocols.
-
Fine-tuning Firewall Policies
Regularly review and fine-tune your firewall policies to align them with your evolving security needs. This includes adjusting access permissions, removing unnecessary rules, and updating rule priorities.
Best Practices for Cloud Security
- Implementing Strong Access Controls
Enforce strong access controls by utilizing secure authentication methods, such as strong passwords or multi-factor authentication (MFA). Restrict access to specifically authorized personnel and regularly review and revoke unnecessary access privileges.
- Regularly Updating and Patching Systems
Regularly updating and patching your cloud systems is crucial for maintaining security. Vulnerabilities and weaknesses can be addressed through timely software updates and patches, ensuring that your infrastructure is protected against known threats.
- Utilizing Intrusion Detection and Prevention Systems
Deploying intrusion detection and prevention systems (IDPS) can significantly enhance your cloud security. IDPS solutions monitor network traffic, detect suspicious activities, and take preventive actions to mitigate potential attacks in real time.
- Enforcing Multi-Factor Authentication
Implementing multi-factor authentication (MFA) adds an extra layer of security to your cloud environment. By obtaining multiple forms of verification, such as passwords and biometrics, you reduce the risk of unauthorized access, even if credentials are compromised.
- Performing Regular Backups and Disaster Recovery Planning
Regularly backing up your cloud data and developing a comprehensive disaster recovery plan are essential for safeguarding against data loss or system failures. In the event of an incident, having reliable backups and a well-defined recovery strategy can minimize downtime and mitigate potential damages.
Advanced Security Measures to Implement

- Network Segmentation
Implementing network segmentation is a proactive measure to enhance security. By dividing your cloud environment into isolated segments, you can restrict access between different components, minimizing the impact of a potential breach and containing threats within a limited area.
- SSL/TLS Certificates and Encryption
Secure Socket Layer (SSL) or Transport Layer Security (TLS) certificates provide secure communication channels between clients and servers. By encrypting data in transit, you ensure that sensitive information remains confidential and protected from eavesdropping or tampering.
- Security Monitoring and Incident Response
Continuous security monitoring allows you to identify and respond to security incidents promptly. Implementing robust security monitoring tools and practices enables real-time threat detection, rapid incident response, and proactive security measures.
- Continuous Security Auditing and Testing
Regular security audits and penetration testing help identify vulnerabilities and weaknesses in your cloud infrastructure. By conducting comprehensive assessments, you can proactively address security gaps and implement necessary remediation measures.
Security Awareness Training for Employees
Ensuring a robust security stance requires the crucial step of educating your employees on the best practices for cloud security. It is imperative to organize frequent training sessions aimed at enhancing awareness about phishing attacks, social engineering techniques, and safe online practices. Foster a culture that emphasizes adherence to security protocols and prompt reporting of any suspicious activities by employees.
Conclusion
Protecting your cloud infrastructure from potential cyber threats is of paramount importance in today’s digital landscape. Vultr Bare Metal’s Firewall provides a powerful solution to augment the security of your cloud environment. By understanding its features and capabilities and following best practices such as strong access controls, regular system updates, and multi-factor authentication, you can fortify your cloud infrastructure against attacks.
Additionally, implementing advanced security measures like network segmentation, encryption, security monitoring, and continuous auditing further strengthens your defense. Remember, cloud security is an ongoing process that requires regular assessment, proactive measures, and employee awareness.
By leveraging the capabilities of Vultr Bare Metal’s Firewall and adopting a comprehensive security approach, you can protect your valuable data and ensure the resilience and reliability of your cloud infrastructure in the face of evolving cyber threats.
FAQs
What advanced security measures can I implement alongside Vultr Bare Metal’s Firewall?
Some advanced security measures include network segmentation to restrict access between different components, implementing SSL/TLS certificates and encryption for secure communication, implementing security monitoring and incident response strategies, conducting regular security audits and testing, and providing security awareness training for employees.
Is cloud security a one-time effort?
No, cloud security is an ongoing process. It requires continuous assessment, proactive measures, and staying updated with the latest security practices and threats. Regular monitoring, auditing, and employee training are essential components of maintaining a strong security posture.
Can Vultr Bare Metal’s Firewall protect against all types of cyber threats?
While Vultr Bare Metal’s Firewall provides a robust security solution, it is important to note that no security measure can guarantee absolute protection against all cyber threats. It is always recommended to employ a multi-layered security approach that includes various security tools, practices, and user awareness.
Can I use Vultr Bare Metal’s Firewall with other cloud providers?
Vultr Bare Metal’s Firewall is specifically designed for Vultr’s cloud infrastructure. While it may not be directly applicable to other cloud providers, similar firewall solutions are typically available from other providers, allowing you to implement similar security measures within their respective platforms.



